Ransomware is a type of malicious software that carries out the cryptoviral extortion attack from cryptovirology that blocks access to data until a ransom is paid and displays a message requesting payment to unlock it. Simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse. More advanced malware encrypts the victim's files, making them inaccessible, and demands a ransom payment to decrypt them.
The ransomware may also encrypt the computer's Master File Table (MFT) or the entire hard drive.Thus, ransomware is a denial-of-access attack that prevents computer users from accessing files since it is intractable to decrypt the files without the decryption key. Ransomware attacks are typically carried out using a Trojan that has a payload disguised as a legitimate file.
Ransomware stops you from using your PC. It holds your PC or files for "ransom". This page describes what ransomware is and what it does, and provides advice on how to prevent and recover from ransomware infections.
You can also read our blog about ransomware: The 5Ws and 1H of ransomware.
On this page:
What does ransomware do?
There are different types of ransomware. However, all of them will prevent you from using your PC normally, and they will all ask you to do something before you can use your PC.
They can target any PC users, whether it’s a home computer, endpoints in an enterprise network, or servers used by a government agency or healthcare provider.
Ransomware can:
- Prevent you from accessing Windows.
- Encrypt files so you can't use them.
- Stop certain apps from running (like your web browser).
Ransomware will demand that you pay money (a “ransom”) to get access to your PC or files. We have also seen them make you complete surveys.
There is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again.
Details for home users
There are two types of ransomware – lockscreen ransomware and encryption ransomware.
Lockscreen ransomware shows a full-screen message that prevents you from accessing your PC or files. It says you have to pay money (a “ransom”) to get access to your PC again.
Encryption ransomware changes your files so you can’t open them. It does this by encrypting the files – see the Details for enterprises section if you’re interested in the technologies and techniques we’ve seen.
Older versions of ransom usually claim you have done something illegal with your PC, and that you are being fined by a police force or government agency.
These claims are false. It is a scare tactic designed to make you pay the money without telling anyone who might be able to restore your PC.
Newer versions encrypt the files on your PC so you can’t access them, and then simply demand money to restore your files.
Ransomware can get on your PC from nearly any source that any other malware (including viruses) can come from. This includes:
- Visiting unsafe, suspicious, or fake websites.
- Opening emails and email attachments from people you don’t know, or that you weren’t expecting.
- Clicking on malicious or bad links in emails, Facebook, Twitter, and other social media posts, instant messenger chats, like Skype.
It can be very difficult to restore your PC after a ransomware attack – especially if it’s infected by encryption ransomware.
That’s why the best solution to ransomware is to be safe on the Internet and with emails and online chat:
- Don’t click on a link on a webpage, in an email, or in a chat message unless you absolutely trust the page or sender.
- If you’re ever unsure – don’t click it!
- Often fake emails and webpages have bad spelling, or just look unusual. Look out for strange spellings of company names (like “PayePal” instead of “PayPal”) or unusual spaces, symbols, or punctuation (like “iTunesCustomer Service” instead of “iTunes Customer Service”).
Check our frequently asked questions for more information about ransomware, including troubleshooting tips in case you’re infected, and how you can backup your files to help protect yourself from ransomware.
Details for enterprises and IT professionals
The number of enterprise victims being targeted by ransomware is increasing. Usually, the attackers specifically research and target a victim (similar to whale-phishing or spear-phishing – and these in fact may be techniques used to gain access to the network).
The sensitive files are encrypted, and large amounts of money are demanded to restore the files. Generally, the attacker has a list of file extensions or folder locations that the ransomware will target for encryption.
Due to the encryption of the files, it can be practically impossible to reverse-engineer the encryption or “crack” the files without the original encryption key – which only the attackers will have access to.
The best advice for prevention is to ensure company-confidential, sensitive, or important files are securely backed up in a remote, un-connected backup or storage facility.
OneDrive for Business can assist in backing up everyday files.Prevalent ransomware
Globally, ransomware continues to be a problem. In particular, we’ve seen increases in Italy and the eastern seaboard of the US.
The past six months (between December 2015 and May 2016) have seen the rise of Tescrypt globally. Crowti remains near the top of the pack, as does Brolo and FakeBsod.
Reveton has also dropped down the ladder, now at 1% of the top 10 share, down from 7% for the preceding 6 months.
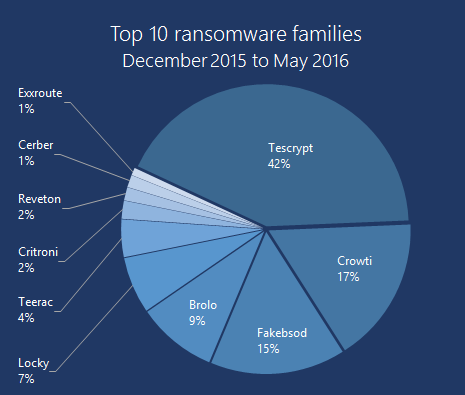
Figure 1. Top 10 Ransomware (December 2015 to May 2016)
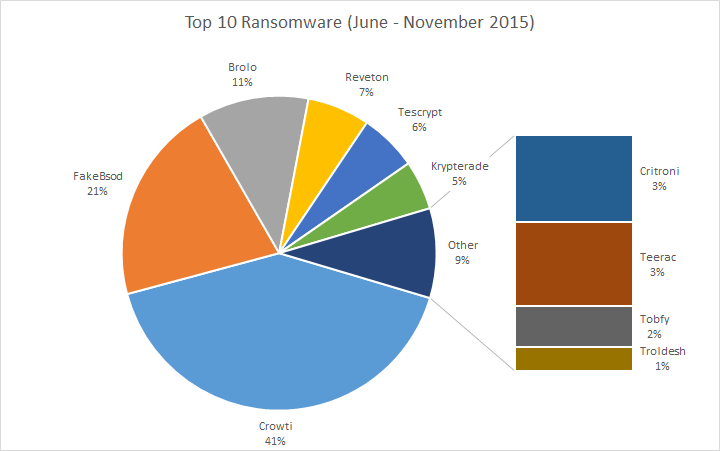
Figure 2. Top 10 Ransomware (June to November 2015)
For the top 10 countries with the most detections, the United States takes a full half of all detections. Italy is second, followed closely by Canada, Turkey, and the United Kingdom. After that the distribution is spread across the globe.
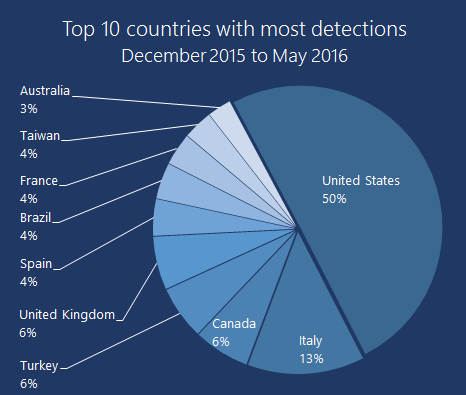
Figure 3: Top 10 countries (December 2015 to May 2016)
The greatest detections in the US were for FakeBsod, followed by Tescrypt and Brolo. Tescrypt was also prevalent in Italy.
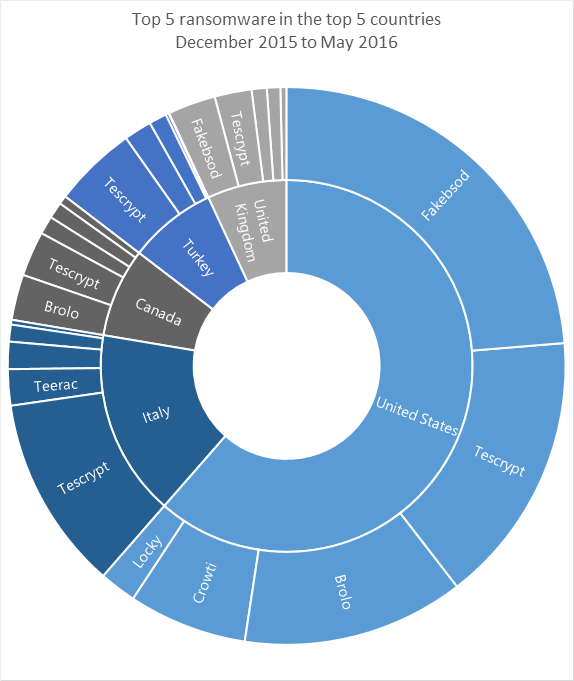
Figure 4: Top detections in top countries (December 2015 to May 2016)
FakeBsod uses a malicious piece of JavaScript code to lock your web browser and show a fake warning message when you visit a compromised or malicious webpage. The warning message tells you to “contact Microsoft technicians” about an “Error 333 Registry Failure of operating system – Host: Blue screen Error 0x0000000CE”. If you call the phone number in the message you will be asked to pay money to “fix” the issue.
An example of the fake warning message is shown in Figure 5:

Figure 5: Message used by FakeBsod to lock your web browser
You can regain control of your web browser without paying anything by closing the warning message using the Task Manager.
WannaCry locks the data on a computer system and leaves the user with two files: instructions on what to do and the Wanna Decryptor program.
Victims have been warned that their files will be deleted within days if they do not pay up using Bitcoin, the world’s biggest virtual currency.
Investors have been scrambling to buy security stocks since the crisis and with many companies shares now at a record high.
Victims are expected to contact the criminals for a key to unlock their files
previously this attack was don by group of hackers on On 12 May 2017,
According to this time this attack is no done by a group of people or by any organization it is done by a single person with lots of knowledge of cyber crime who may be technician of any it company or any countries cyber team member who has a reach to database of almost all countries.
i only do have a solution is to have a kill switch and a registered domain .
and only a way to stop this attack is to register the hackers broadcast with a domain which should be non accessible .
other such good option is to stop trading of bitcoins which will forcefully stop the hacker/hackers to stop their farewell.
No comments:
Post a Comment