Facts
Monday, October 1, 2018
Astronomers Have Found a Strange Neutron Star That "Shouldn't Exist"

Sunday, September 30, 2018
This New Lithium Battery Tech Can Simply Suck Up CO2 to Power Itself
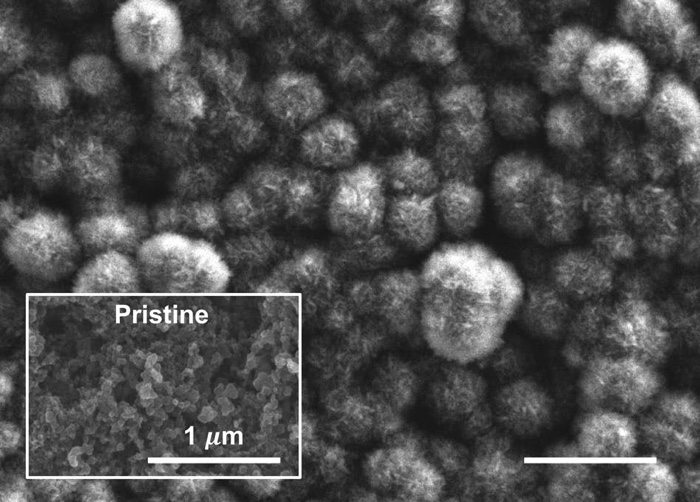 The cathode after discharge, showing carbonate material derived from emissions, and the pristine, pre-discharge surface. (MIT)
The cathode after discharge, showing carbonate material derived from emissions, and the pristine, pre-discharge surface. (MIT)Sunday, September 3, 2017
Experts Cast Doubt on Groundbreaking CRISPR Embryo Editing Research
**********What did CRISPR actually do to the embryos?**********

Scientists Have Found a Completely New Way to Attack And Kill Cancer Cells
**********If this works in people, it will be better than chemo.**********
We May Have Finally Discovered The Trigger That Starts Autoimmune Diseases
**********When the body attacks itself.**********
Tuesday, May 16, 2017
How to get over wanacry
1. Let the ransom work as it want.
2. After the time is completed you have three options to get your files and folder back
1. Right click on my computers and go for configuration of disk managment and just restore each and every drive so that you can restore your folders according to last configurations before the changes was done to your storage.
2. Format your pc completely.
Install windows.
Instal a software called recuva or esus data manager.
In recuva first you have to go to a wizard for recovery of type of file 》select storage location》enable deep scan》 select advance mode so that you can get files with preview and it is must to configure a box : save before encryption so that you get original file.
:* using easus data managment recover the data according to asked configuration
3. Plug out or disconnect the internet
Change the date and time of the pc or lappy .
Copy the data to another storage without opening files.
Any of the above methods will be over written by hackers as they get to know it.
Hurry before they get it done
Tc * any of the method is not gaurenteed it is humble request to try on own responsiblity.
Ransomeware as wanacry making whole world technisions cry
What does ransomware do?
- Prevent you from accessing Windows.
- Encrypt files so you can't use them.
- Stop certain apps from running (like your web browser).
Details for home users
- Visiting unsafe, suspicious, or fake websites.
- Opening emails and email attachments from people you don’t know, or that you weren’t expecting.
- Clicking on malicious or bad links in emails, Facebook, Twitter, and other social media posts, instant messenger chats, like Skype.
- Don’t click on a link on a webpage, in an email, or in a chat message unless you absolutely trust the page or sender.
- If you’re ever unsure – don’t click it!
- Often fake emails and webpages have bad spelling, or just look unusual. Look out for strange spellings of company names (like “PayePal” instead of “PayPal”) or unusual spaces, symbols, or punctuation (like “iTunesCustomer Service” instead of “iTunes Customer Service”).
Details for enterprises and IT professionals
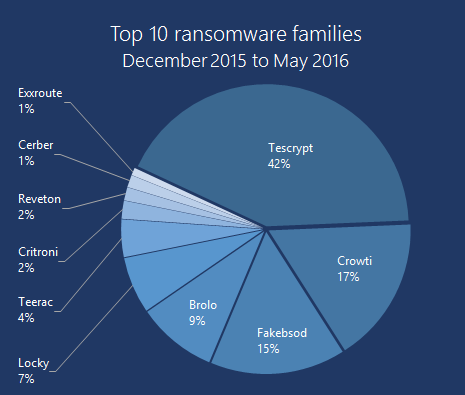
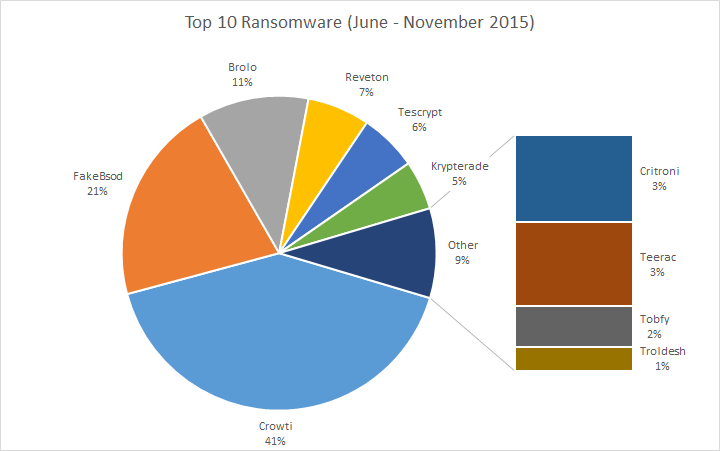
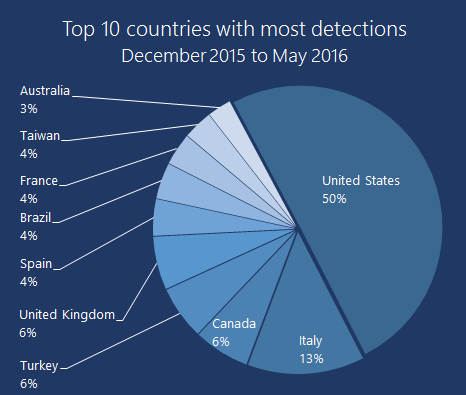
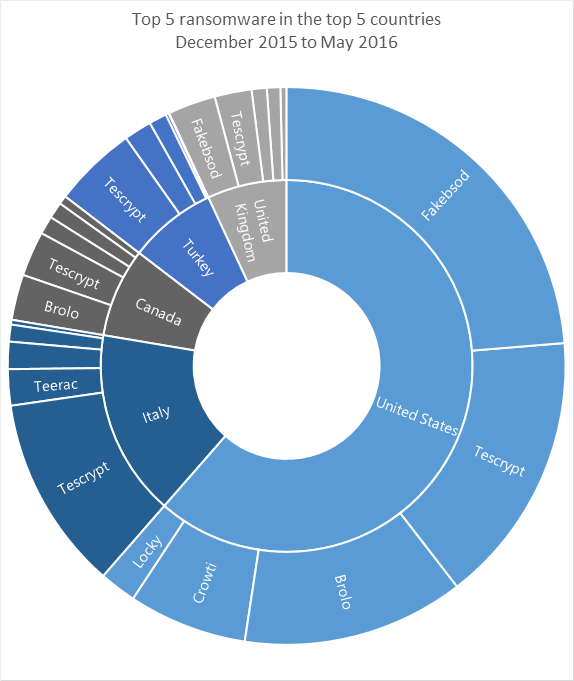
Prevalent ransomware